HAWK.io MDR
Real-Time Threat Containment-As-A-Service Before Busines Impact
See Why HAWK is Different
CISOs and SOC Teams Must Know What is Happening in Real-Time On Their Business Networks Right Now
HAWK Technology. Cloud-based. Multi-Tenant.
SIEM and MDR solutions all have a common denominator: they all focus on ‘what has happened’ and interrogate mountains of historical log data, searching for the evidence necessary to prove or disprove a malicious exploit has occurred.
It is time to move beyond chasing alerts, manual inspection, and association of potential malicious indicators. Vulnerability-based cybersecurity strategies are tied to a historical view of security events and fulfill specific objectives but are impractical for efficient, effective threat containment.
Efficient. Effective. Business Aligned.
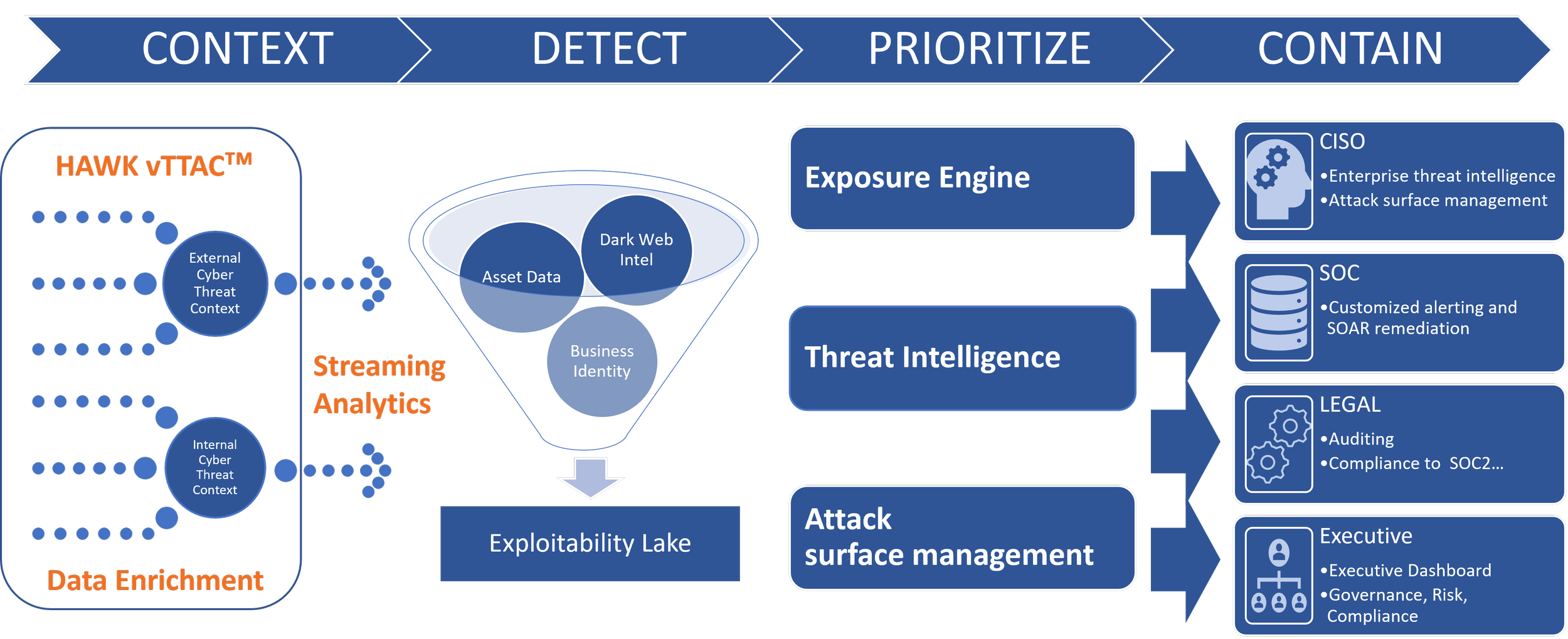
To address today’s high-volume/high-velocity threat environment, HAWK.io MDR delivers advanced automation of SOC incident handling on live streaming enhanced telemetry data.
A resilient cybersecurity strategy focuses on real-time enriched telemetry data and AI/ML that accurately automate tedious and error-prone L1/L2 threat-hunting tasks and supports L3 SOC analysts with automated exploit containment capabilities. Exploit containment core metrics are the time to detect, time to escalate, time to contain, and business impact are readily available and valuable for C-level briefings.

Business Impact Reporting
CISOs must present information demonstrating the alignment of incident response efforts with the company's goals
Measurable metrics include:
Time to Detection
Time to Escalation
Time to Containment
Business Impact
It is powerful to be able to report that an incident in question was:
“Detected in 5 seconds, escalated in 30 seconds, and contained within 10 minutes. There was no evidence of material loss of operations, data exfiltration, or brand damage.”
Actual Customer Experience
HAWK.io provides SOC performance data in a C-suite caliber narrative to the CISO.
Not All Telemetry Data Is the Same
Effective incident response requires you to have the entire picture before making a crucial decision that could impact your business. HAWK vTTACᵀᴹ complements existing end-point detection controls by enriching every event with additional information related to the active incident.
HAWK.io automates the artifact collection and digital forensics and incident response (DFIR) so that customers have all of the associated incident information organized in one place and ready for incident containment and response.
HAWK.io + vTTAC™
-
Automatically collects real-time machine data and raw logs from Windows and Unix servers, including important details and context far beyond what typical Windows and Unix system logs contain.
-
Gathers artifacts in support of Digital Forensics/Incident Response (DFIR) efforts
-
EventX enriches key/value pairs of each event based on process and user information into each event record to improve the accuracy of analytics. See what parent process called each event, command line, etc., beyond what Windows logs provide.
-
Easy-to-deploy real-time monitoring in virtual environments (Cloud Agnostic)
-
Automates the installation and configuration management of Sysmon to ensure proper enhanced logging is maintained
-
File Integrity Monitoring, Command Normalization, Command Obfuscation Detection
-
Automatically maintains all required logging settings through a device outage or software upgrade.
-
HAWK’s patented data normalization process protects against costly, bloated data lakes. vTTAC™ controls what records and even what fields within records are captured in real-time. No need for 3rd-party data management tools.

Contain Exploits Before Impact to Operations
HAWK.io MDR Combines the Advanced Science of Streaming Analytics With AI/ML to Automate Investigations
HAWK.io’s advanced incident response capabilities focus on containing live exploits to mitigate the material loss of assets, profitability, or brand damages.
HAWK.io is built entirely on HAWK technology and features patented data enrichment (vTTACᵀᴹ) client and streaming analytics (vStreamᵀᴹ) technologies.
HAWK.io MDR eliminates the need for SOC analysts to conduct long manual inspection and diagnosis cycles and catches threats that other SIEM-based MDRs and EDR/XDR products miss.
-
• Behavioral-based Anomaly Detection
• Signature-based (known exploits)
• Dark Web Monitoring
• Leverages Threat Intel data:
o HAWK proprietary feeds
o Third-party feeds
o Custom feeds
• Uses MITRE ATT&CKᵀᴹ Matrix for tactics, techniques, and procedures to support:
o Detection and classification of incidents
o Threat mitigation/protection
o Recovery
-
• Detect non-signature-oriented low-level cyber-attacks such as:
o Living Off the Land
o Beacon Detection
o Domain Generated Algorithms (ransomware)
• Malicious Web Requests
• Incorporates intrusion detection data feeds
• Leverages Threat Intel data:
o HAWK proprietary feeds, Third-party feeds, Customer-developed feeds